Binary Vulnerability Analysis
About Binary Vulnerability Analysis
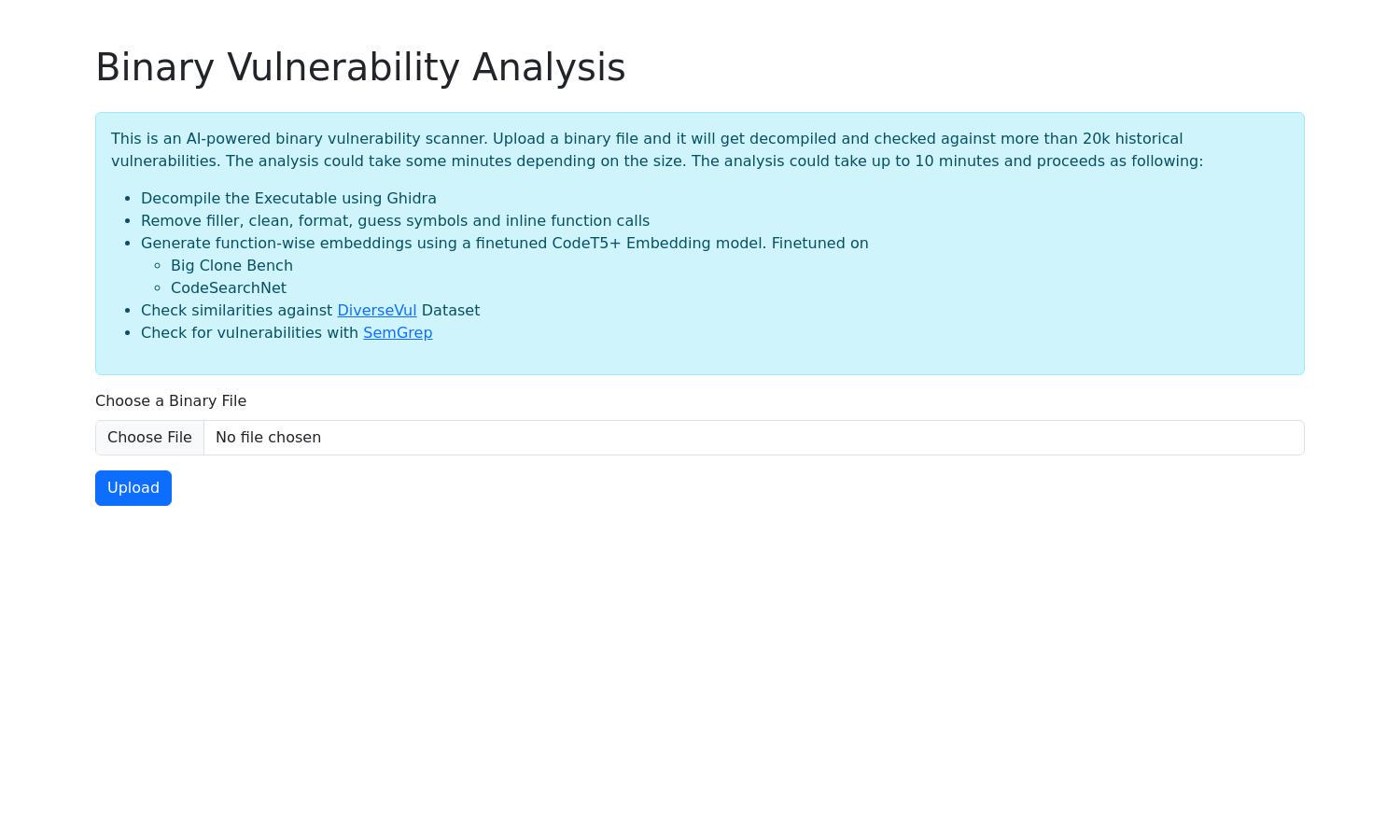
Binary Vulnerability Analysis is an AI-based platform designed to identify vulnerabilities in binary files. Users upload binaries, which are decompiled and analyzed against a database of over 20,000 historical vulnerabilities, offering essential security assessments to developers and security professionals eager to maintain software integrity.
Binary Vulnerability Analysis offers flexible pricing plans. Each tier is designed to cater to various user needs, providing value through comprehensive vulnerability scanning. Upgrading grants additional features and deeper insights, ensuring users maximize their security assessments while maintaining a robust defense against potential threats.
The user interface of Binary Vulnerability Analysis is intuitively designed for seamless interaction. With easy navigation and user-friendly features, it enhances the browsing experience, allowing users to focus on vulnerability assessment without distraction, ensuring maximum efficiency in managing binary file security.
How Binary Vulnerability Analysis works
Users interact with Binary Vulnerability Analysis by simply uploading their binary files through an easy-to-navigate web interface. The platform then decompiles the executable file using advanced algorithms, cleans and formats the code, before applying AI models to identify vulnerabilities, providing straightforward security insights in a few minutes.
Key Features for Binary Vulnerability Analysis
AI-Powered Binary Scanning
Binary Vulnerability Analysis features an AI-powered binary scanning system that accurately identifies vulnerabilities. By leveraging advanced decompilation techniques, this unique feature ensures that users receive precise insights, allowing developers to proactively rectify security flaws and enhance software resilience.
Vulnerability Database Access
The platform offers access to a vast vulnerability database, including over 20,000 historical vulnerabilities. Binary Vulnerability Analysis enables users to check their binaries against this extensive dataset, ensuring comprehensive assessments that empower developers to swiftly address potential security risks in their applications.
Detailed Decompilation Process
The detailed decompilation process utilized by Binary Vulnerability Analysis stands out for its thoroughness. By removing fillers and guessing symbols accurately, users gain a clear and structured analysis of their binary files, facilitating improved security assessments and more effective vulnerability remediation.
You may also like: